Platform security
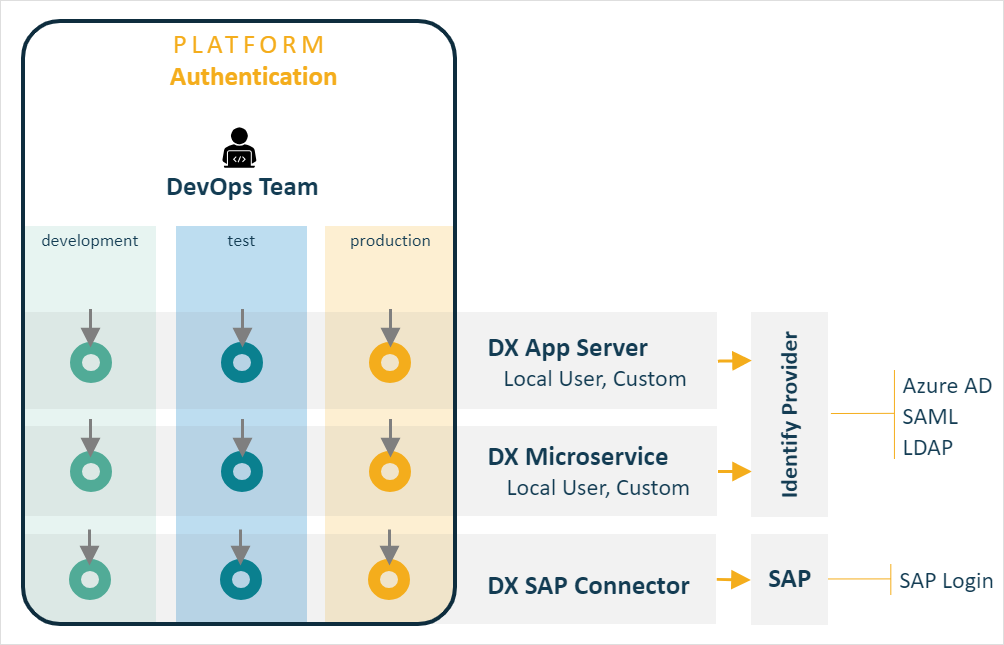
The careful management of access credentials is the foundation to secure access to Neptune DXP and its individual functions. Every interaction with the platform must be automatically authorised. Establishing an appropriate credential management practice will allow you to tie the use of Neptune DXP to your DevOps roles and ensure that only authenticated and authorised parties access your platform.
Authentication
Neptune DXP supports the following user authentication protocols:
-
Microsoft Entra ID
-
SAML federated identities
-
LDAP Integration – for example, on-premise Microsoft Active Directory or other LDAP solution
-
Local User Store when access to an IDP service is not wanted or feasible
-
Custom Authentication, allowing the use of a bespoke script driven mechanism to be built
Authorisation
First steps
When you install a Neptune DXP server you will begin with an initial identity that has access to all Neptune DXP functions. This initial user (known as the admin user) isn’t intended for everyday tasks, and its credentials should be carefully protected. You use this identity to establish less-privileged platform users and role-based access in the Neptune DXP security roles and access control level function.
Let’s look at an example of a DevOps team with the following, indicative, roles:
| Development | Operations |
|---|---|
Frontend Developer |
Infrastructure Engineer |
Backend Developer |
Security Engineer |
Test Engineer |
Release Manager |
The infrastructure engineer may be tasked with the provisioning of the Neptune DXP on your infrastructure of choice. Once installed they log in for the first time using the admin user. After making several initial settings they conclude by defining in Neptune DXP Security a new role to represent the security engineer. The scope of access awarded is limited to security related tasks, including the setup of additional roles.
Building out
The security engineer then establishes all the remaining DevOps roles with appropriate access levels, for example:
-
Backend developer with access to develop server scripts, configure APIs and request the transfer of deployment packages
-
Infrastructure engineer has system settings such as database connectivity and external services such as email or Firebase notifications as well as access to monitor logs
-
Release manager has access to approve deployment packages
Then continue until all roles are filled.
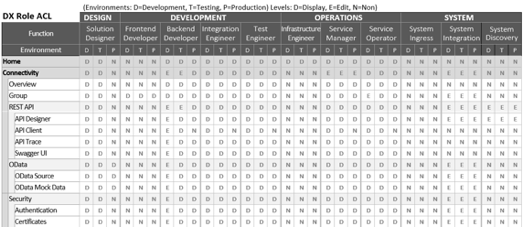
Fine-grained control
Neptune DXP supports role-based access control to its functions allowing you to establish a principle of least privilege so that authenticated identities are only permitted to perform a minimal set of functions necessary to fulfil specific tasks. This limits the blast radius if unauthorised access is obtained and allows you to enforce the segregation of duties for oversight and governance. A role-based matrix such as the one shown below can be modelled into DX’s Platform Access Level Control function to segregate duties.