User management for Cockpit authorization
From version 5.3.6 it is possible to restrict access in the Cockpit to certain menu entries. It is also possible to separate between read- and write-access in the Cockpit.
Starting from version 5.3.6, Neptune Cockpit includes access control. It provides a Neptune authorization object and several authorization roles included in the installation package. These roles can be managed in transaction PFCG. User assignment of these roles can also be done in transaction PFCG or individually in transaction SU01.
Neptune Standard Roles
These are the predefined roles included in the installation package:
-
/NEPTUNE/ADMIN- Neptune Administrator role -
/NEPTUNE/DESIGNER- Neptune DXP Designer -
/NEPTUNE/DEVELOPER- Neptune Developer Role -
/NEPTUNE/READ_ONLY- Display access for all Cockpit apps -
/NEPTUNE/TEMPLATE_COCKPIT_APPS- Template role containing a list of all Cockpit apps
More detailed explanations of each predefined role:
/NEPTUNE/ADMIN-
This role grants access to all menus and functions in Neptune Cockpit.
/NEPTUNE/DESIGNER-
In addition to the SAP GUI transactions, this role only grants access to the App Designer in the Neptune Cockpit.
/NEPTUNE/DEVELOPER-
The traditional Developer role grants access to all development and admin tasks of the Neptune Platform.
/NEPTUNE/READ_ONLY-
This role grants display access to all Cockpit apps, but users are restricted from performing any changes.
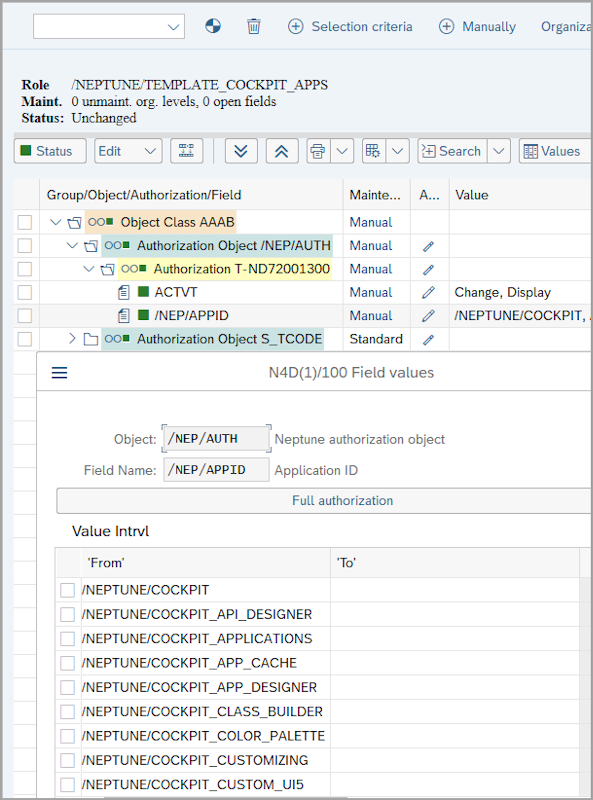
/NEPTUNE/TEMPLATE_COCKPIT_APPS-
This role contains a list of all Cockpit apps and can be used as a template for restricting access to certain menu options or functions. You can make a copy of this role and remove apps or functions according to your needs.
This is what it will look like for users who have no access to the Cockpit:
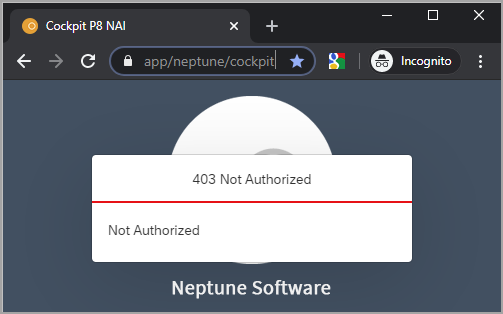
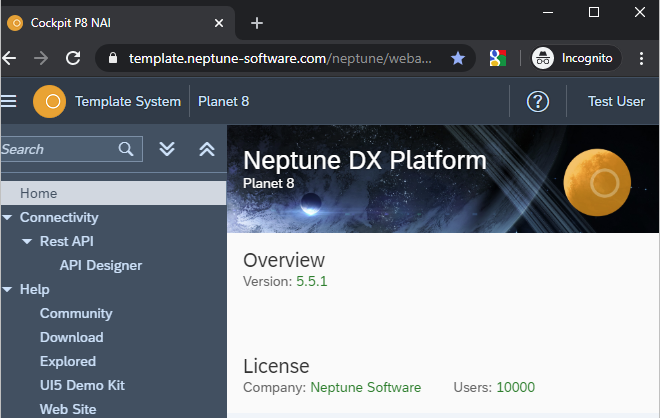
For instance, with only access to the API Designer the menu will look like this:
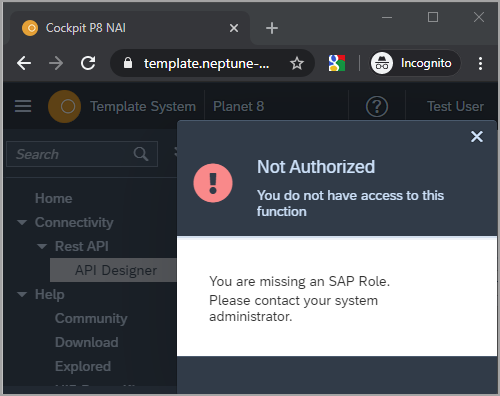
When trying to Add, Edit or Delete and the user only have read-only access, this message is displayed:
Custom Authorization Checks
In the Neptune Cockpit, custom authorization checks are performed using the authorization object /NEP/AUTH. When adding
custom authorization checks within your custom apps, you can also use this same authorization object. Corresponding ABAP
code should be added in the application class.
Check for Read Access
To check for read access, you can use the following ABAP code:
" Read access?
authority-check object '/NEP/AUTH'
id 'ACTVT' field '03'
id '/NEP/APPID' field applid.
if sy-subrc ne 0.
" Provide an error message to the user or return
return.
endif.Check for Write Access
To check for write access, you can use the following ABAP code:
" Write access?
authority-check object '/NEP/AUTH'
id 'ACTVT' field '02'
id '/NEP/APPID' field applid.
if sy-subrc ne 0.
" Provide an error message to the user or return
return.
endif.Neptune Authorization Object
The authorization object /NEP/AUTH is included in the /NEPTUNE/DEVELOPER role with full access to the Cockpit apps.
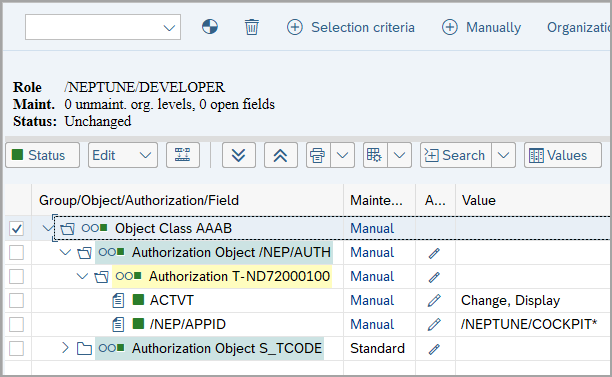
To limit access, you can create a copy of the /NEPTUNE/TEMPLATE_COCKPIT_APPS role and adjust it accordingly.
Deprecated Authorization Object
In previous versions (5.3.6 - 5.4.7), the custom authorization object Y_NEPTUNE was included in the installation.
The authorization checks in the Neptune Cockpit are still backwards compatible, so you may still use roles containing
this object. However, all new roles and checks will be made using the new object /NEP/AUTH.