SAP principal propagation
Overview
SAP Principal Propagation allows destinations to forward the identity of an on-demand user to the back-end system of the relevant SAP on-premises system or cloud system. An on-demand user does not need to provide an identity for each connection to an SAP system when using Neptune DXP - Open Edition. The identity is instead propagated through Principal Propagation.
When to use principal propagation
You can use Principal Propagation if the back-end service endpoint accepts client certificate authentication for both SAP and non-SAP systems. This can be used with HTTPS protocol or RFC protocol with SAP Secure Network Communications (SNC). You can generate an X.509 certificate using Neptune DXP - Open Edition.
Technical scenario
In almost all applications, the identity of a user needs to be verified against the back-end system. In Neptune DXP - Open Edition, one of the ways to do that is to use Principal Propagation with X.509 certificates. Once the user has been verified against an identity provider (IdP), a short-lived certificate is generated that can be passed along with the request to the back-end system. The identity of the user between the Neptune DXP - Open Edition and back-end system should be the same when accessing the system to achieve single sign-on login.
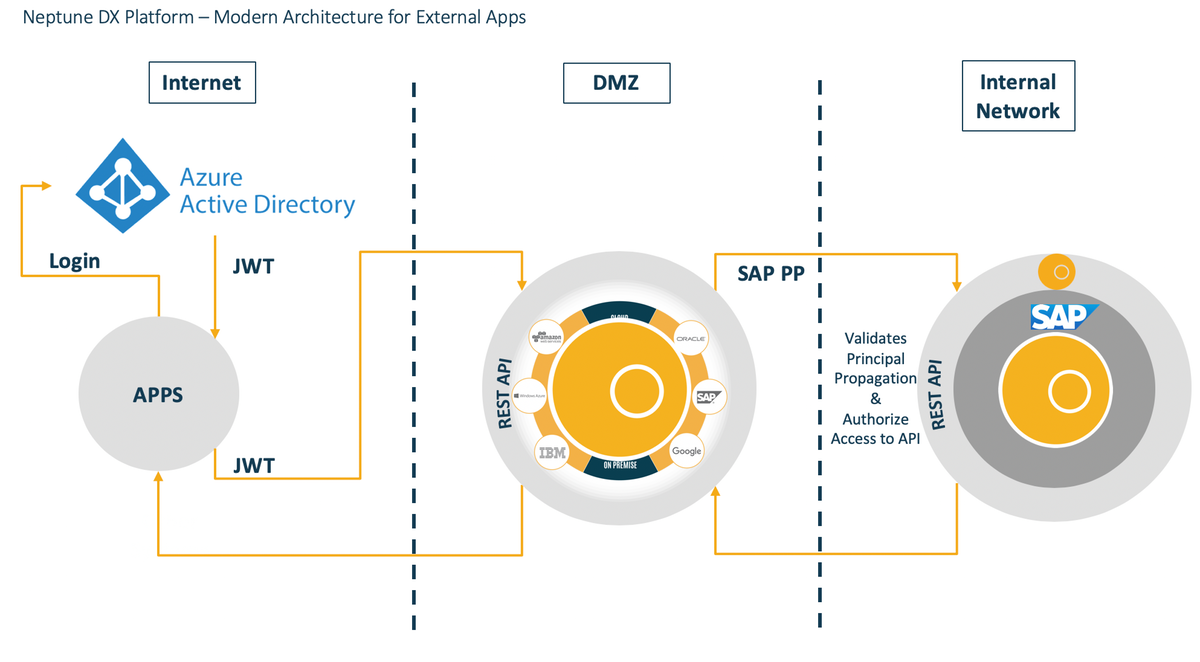
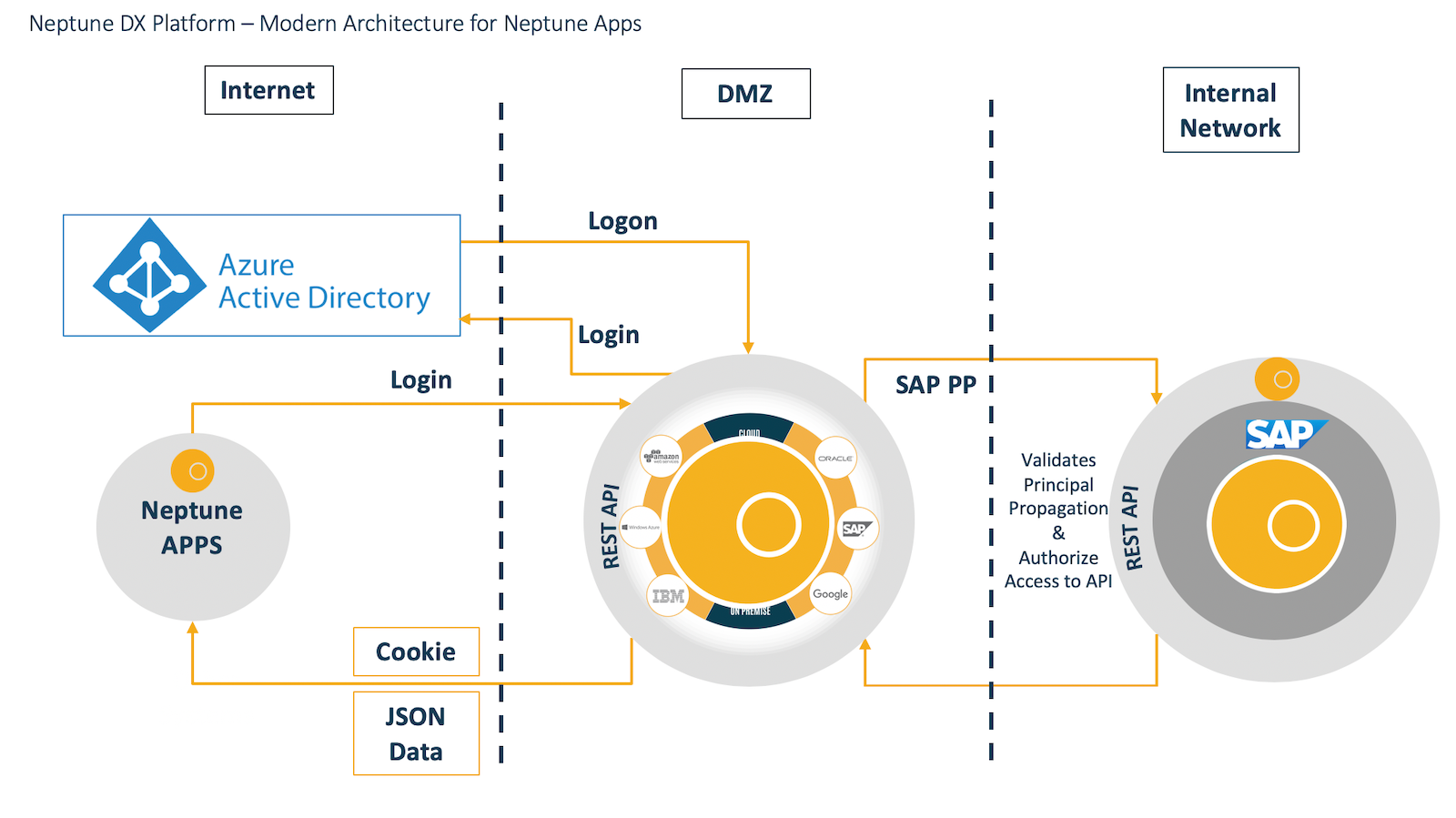
Value proposition
Having Principal Propagation enabled on Neptune DXP - Open Edition allows the user to access a resource without needing to provide an identity every time the user makes a connection to the on-premises system or SAP Cloud.
This is a one-time setup per back-end system so the time and effort for this is short and any new business scenario that uses the same back-end system are ready to go. This type of user identity propagation method allows Neptune DXP - Open Edition to consume a variety of back-end systems that accept X.509 certificate-based authentication.
Related topics
-
Enabling principal propagation in Neptune DXP - Open Edition
-
SAP help: Principal Propagation setup between Cloud Platform and on-premise backend system
-
SAP help: Configuring the System to Use the SAP Trust Center Service
-
For tracing or debugging, use the report SEC_TRACE_ANALYZER in SE38 in SAP.
-