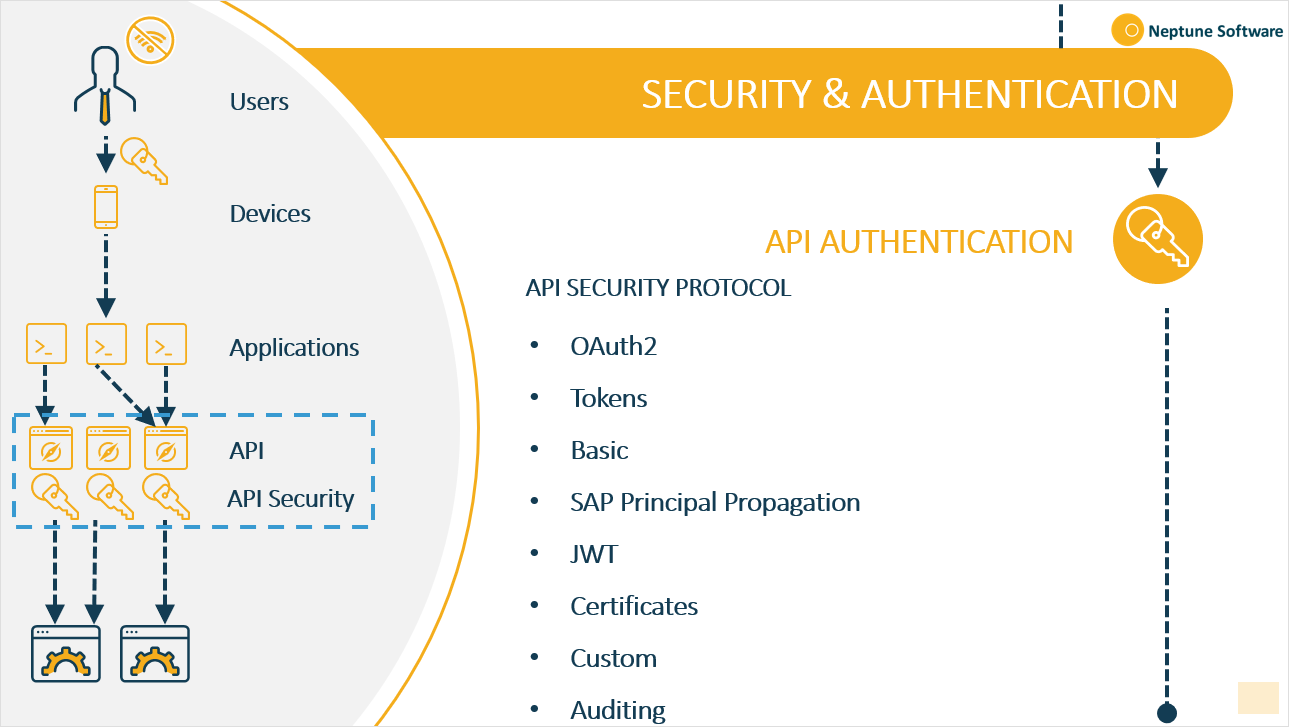
API authentication
At some point, your APIs need to allow limited access to users, servers, or servers on behalf of users. As APIs handle enormous amounts of critical data, securing these connections is important.
Neptune DXP - Open Edition supports the following API authentication methods:
Auditing
When a user creates, updates, or deletes an entity, that operation is added to Audit Log, along with the timestamp, username and content of the operation.
The Audit Log interface is read-only in Neptune DXP - Open Edition and should be made visible to users that need this kind of functionality only.
oAuth 2.0
By using the oAuth 2.0 authentication framework, you can provide your applications to users with limited access to your APIs on behalf of the application itself.
Basic
You can enable basic API authentication by requesting a username and password to validate a user’s identity and access permissions.
SAP Principal Propagation
Enable SAP Principal Propagation to set up API authentication with SAP Cloud or SAP on-premise.
Tokens - JWT
If you do not want to use any of the authentication types above, you can enable the Neptune DXP - Open Edition token-based authorisation by an JWT Bearer token.
Certificates
Certificate-based authentication works with two parties verifying the others provided digital certificates. In technology terms, it refers to a client (web browser or client application) authenticating themselves to a server (website or server application). That server also authenticates himself to the client by verifying the public key certificate/digital certificate issued by the trusted Certificate Authorities (CAs).
In Neptune DXP - Open Edition, you can generate a self-signed certificate to access the authorised resource or import the certificate from the authorised resource.
Customised authentication
Instead of predefined authentication methods you can also define a new method by writing your own JavaScript code and include your own node.js modules.
Be careful with what you make accessible to external systems and what is accessible through the API. For example, if a script accesses another decrypted database, an external user might be able to pick up the username and password if that is part of the connection string.
In general, having access to server scripts gives you a lot of power. Keep that in mind when deciding who you give access to.